
SSL Checker Online Tool: Complete Guide to Website Security
The Ultimate Guide to Using an SSL Checker Online Tool for Website Security
In today's digital landscape, website security isn't optional—it's essential. Every day, countless websites fall victim to data breaches, hacking attempts, and security vulnerabilities that compromise both business integrity and user trust. Fortunately, implementing SSL (Secure Sockets Layer) encryption is one of the most effective ways to protect your website and its visitors. To ensure your SSL certificate is properly configured and functioning, you need a reliable ssl checker online tool that can diagnose issues and verify your security implementation.
This comprehensive guide will walk you through everything you need to know about SSL certificates, how to use SSL checker tools effectively, and how to interpret the results to maximize your website's security. Whether you're a complete beginner or an experienced webmaster, you'll find valuable insights and practical steps to enhance your website's security posture.
What Is SSL and Why Does Your Website Need It?
SSL (Secure Sockets Layer) is a standard security technology that establishes an encrypted link between a web server and a browser. This encrypted connection ensures that all data transferred between the server and browser remains private and integral. SSL is the predecessor to TLS (Transport Layer Security), though the terms are often used interchangeably.
The Evolution of SSL to TLS
SSL was originally developed by Netscape in the 1990s to ensure secure internet transactions. However, due to discovered vulnerabilities, SSL has been largely replaced by TLS, which offers stronger security algorithms and improved protocols. Despite this technical evolution, "SSL" remains the more commonly used term in the industry, and most "SSL certificates" actually implement TLS protocols.
How SSL/TLS Encryption Works
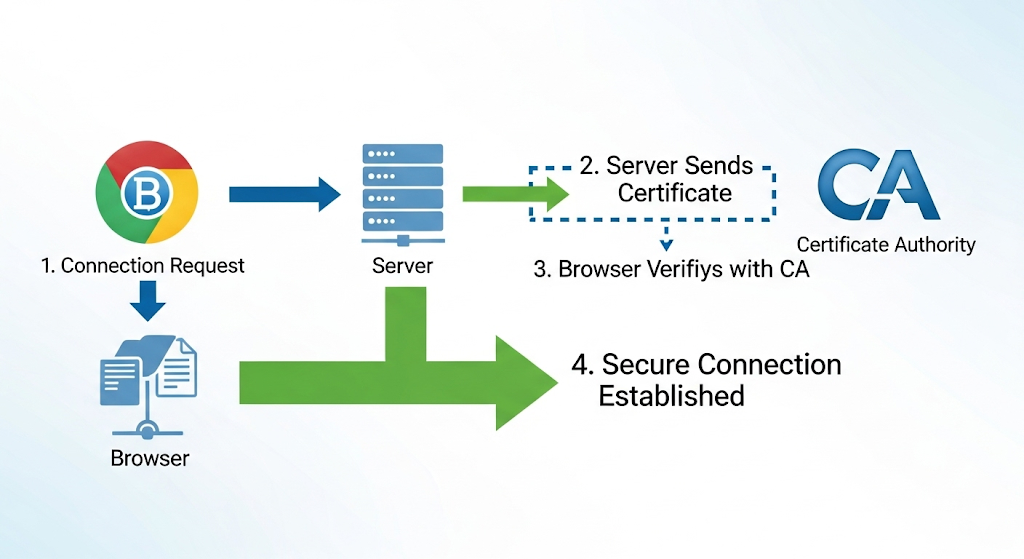
When a visitor accesses an SSL-secured website, their browser and the server perform what's called an "SSL handshake." This process involves:
- Browser Request: The browser requests a secure connection from the server.
- Server Response: The server sends its SSL certificate, which contains its public key.
- Verification: The browser verifies the certificate with the issuing Certificate Authority (CA).
- Key Exchange: Once verified, the browser generates a symmetric session key and encrypts it with the server's public key.
- Secure Session: The server decrypts the session key with its private key, and both parties now have a shared secret key for encrypting and decrypting data during the session.
This entire process happens in milliseconds and is completely transparent to the user, except for visual indicators like the padlock icon in the browser's address bar.
Why SSL Is Non-Negotiable for Modern Websites
Implementing SSL on your website is no longer optional—it's a critical requirement for several reasons:
Data Protection: SSL encryption protects sensitive information such as login credentials, credit card numbers, and personal data from interception by malicious actors.
User Trust: Visual indicators like the padlock icon and "https://" in the address bar signal to visitors that your website is secure, increasing their confidence in your business.
SEO Benefits: Since 2014, Google has used HTTPS as a ranking signal. Websites with SSL certificates typically rank higher in search results than their non-secure counterparts.
Browser Warnings: Modern browsers like Chrome, Firefox, and Safari display prominent warnings when users visit non-secure websites, potentially driving away visitors.
Payment Card Industry (PCI) Compliance: If your website processes credit card payments, SSL encryption is mandatory for PCI compliance.
Regulatory Requirements: Data protection regulations like GDPR and CCPA require appropriate security measures for handling personal information, with SSL being a fundamental component.
Understanding SSL Certificates: Types and Validation Levels
Before diving into SSL checker tools, it's essential to understand the different types of SSL certificates available and their varying levels of validation. This knowledge will help you interpret the results from SSL checkers and make informed decisions about your website's security.
SSL Certificate Types
SSL certificates come in several types, each designed for different use cases:
1. Domain Validated (DV) Certificates
DV certificates offer basic encryption and are the easiest and quickest to obtain. The Certificate Authority (CA) only verifies that the applicant owns the domain name, typically through email verification or DNS record confirmation.
Characteristics:
- Lowest cost (often free)
- Fastest issuance (usually within minutes)
- Basic encryption only
- No organization information displayed
Best for:
- Personal websites
- Blogs
- Small business websites not handling sensitive data
- Development and testing environments
2. Organization Validated (OV) Certificates
OV certificates provide a higher level of validation and trust. The CA verifies the applicant's right to use the domain and conducts some vetting of the organization.
Characteristics:
- Moderate cost
- Issuance typically takes 1-3 days
- Displays organization information in certificate details
- Higher trust level than DV certificates
Best for:
- Corporate websites
- E-commerce sites handling low to medium volume transactions
- Non-profit organizations
- Government agencies
3. Extended Validation (EV) Certificates
EV certificates offer the highest level of validation and trust. The CA conducts a thorough background check of the organization before issuing the certificate.
Characteristics:
- Highest cost
- Longest issuance time (1-2 weeks typically)
- Displays organization name prominently in the browser address bar
- Highest trust level with visible indicators
Best for:
- Financial institutions
- Large e-commerce platforms
- Healthcare organizations
- Government websites handling sensitive data
SSL Certificate Coverage Types
Beyond validation levels, SSL certificates also differ in terms of what they protect:
1. Single-Domain Certificates
These certificates secure only one specific domain (e.g., www.yourdomain.com). They cannot be used for subdomains or different domain names.
2. Wildcard Certificates
Wildcard certificates secure a domain and all its subdomains (e.g., *.yourdomain.com covers www.yourdomain.com, blog.yourdomain.com, shop.yourdomain.com, etc.).
3. Multi-Domain Certificates (MDC/SAN)
Multi-domain certificates can secure multiple different domains and subdomains with a single certificate. They're also known as Subject Alternative Name (SAN) certificates.
4. Unified Communications Certificates (UCC)
UCC certificates are specifically designed for Microsoft Exchange and Office Communications environments, though they can also be used for regular websites.
Certificate Authority Hierarchy
Understanding the certificate authority hierarchy is crucial for interpreting SSL checker results:
Root Certificate Authorities: These are the top-level CAs that issue certificates to Intermediate CAs. Their root certificates are embedded in browsers and operating systems.
Intermediate Certificate Authorities: These CAs receive certificates from Root CAs and issue end-entity certificates to websites. They create a chain of trust between the root certificate and the website's certificate.
End-Entity Certificates: These are the SSL certificates installed on web servers, issued by Intermediate CAs.
When an SSL checker verifies your certificate, it validates this entire chain to ensure each link is properly configured and trusted.
The Critical Importance of SSL Certificate Management
Proper SSL certificate management goes beyond simply installing a certificate and forgetting about it. Active monitoring and maintenance are essential to ensure continuous security and avoid costly disruptions.
Common SSL Certificate Issues and Their Impact
Expired Certificates: When SSL certificates expire, browsers display security warnings that can drive away visitors and damage your reputation. According to Google's Transparency Report, approximately 10% of certificate connections use expired certificates.
Misconfigured Certificates: Improperly configured certificates can lead to partial encryption, security vulnerabilities, and browser warnings. The SSL Pulse project by Qualys found that around 80% of SSL-enabled websites have some configuration issues.
Weak Encryption: Using outdated protocols or weak cipher suites can leave your website vulnerable to attacks like POODLE, BEAST, or Heartbleed.
Incomplete Certificate Chains: Missing intermediate certificates can cause validation failures on some devices and browsers, leading to security warnings for affected users.
Mixed Content: Loading HTTP resources on an HTTPS page can break the padlock indicator and create security vulnerabilities.
The Cost of SSL Certificate Failures
The consequences of SSL certificate issues extend beyond mere inconvenience:
Loss of Visitor Trust: Security warnings can cause up to 85% of visitors to abandon a website, according to HubSpot research.
SEO Penalties: Google explicitly uses HTTPS as a ranking signal, and security issues can negatively impact your search visibility.
Revenue Loss: For e-commerce sites, even brief SSL issues can result in significant lost sales during the outage period.
Security Breaches: Vulnerable SSL configurations can expose sensitive user data, leading to data breaches with potential legal and financial consequences.
Compliance Violations: Many industries have regulatory requirements for data security, and SSL failures can result in non-compliance penalties.
Best Practices for SSL Certificate Management
To avoid these issues, implement these SSL certificate management best practices:
Regular Monitoring: Use SSL checker tools to monitor your certificate status continuously or at least weekly.
Expiration Tracking: Maintain a calendar of certificate expiration dates and set up renewal reminders well in advance.
Automated Renewal: Where possible, implement automated certificate renewal processes, especially with free certificates like Let's Encrypt.
Protocol and Cipher Updates: Regularly review and update your SSL/TLS protocols and cipher suites to ensure you're using the most secure options.
Complete Certificate Chains: Ensure all intermediate certificates are properly installed to maintain the chain of trust.
Mixed Content Resolution: Regularly scan for and fix any mixed content issues that could compromise your HTTPS implementation.
Introducing the SEOMagnate SSL Checker Online Tool
To effectively manage your SSL certificates and ensure optimal website security, you need a reliable and comprehensive SSL checker tool. The SEOMagnate SSL Checker is designed to provide detailed insights into your SSL certificate configuration, identify potential issues, and offer actionable recommendations for improvement.
Key Features of the SEOMagnate SSL Checker
Comprehensive Certificate Analysis: The tool examines every aspect of your SSL certificate, from basic information to advanced configuration details.
Chain Validation: It verifies the complete certificate chain to ensure proper trust relationships between your certificate, intermediate certificates, and root certificates.
Protocol and Cipher Assessment: The tool evaluates your SSL/TLS protocol support and cipher suite configuration to identify potential vulnerabilities.
Security Vulnerability Detection: It checks for known SSL/TLS vulnerabilities and configuration issues that could compromise your website's security.
Expiration Tracking: The tool provides clear information about your certificate's validity period and upcoming expiration dates.
Mobile Compatibility Check: It assesses how your SSL implementation performs across different devices and browsers, including mobile platforms.
Performance Impact Analysis: The tool evaluates how your SSL configuration affects website loading times and provides optimization recommendations.
Actionable Recommendations: Beyond identifying issues, the tool offers specific, actionable steps to resolve any detected problems.
How to Use the SEOMagnate SSL Checker
Using the SEOMagnate SSL Checker is straightforward and requires no technical expertise:
Visit the Tool: Navigate to https://seomagnate.com/ssl-checker
Enter Your Domain: Type your website domain name (e.g., www.yourdomain.com) into the input field. You can include the protocol (https://) or just the domain name.
Initiate the Check: Click the "Check SSL" button to start the analysis. The tool will connect to your server and examine your SSL certificate configuration.
Review the Results: Within seconds, you'll receive a comprehensive report detailing your SSL certificate status, configuration, and any identified issues.
Take Action: Use the provided recommendations to address any identified problems and improve your SSL implementation.
Interpreting SEOMagnate SSL Checker Results
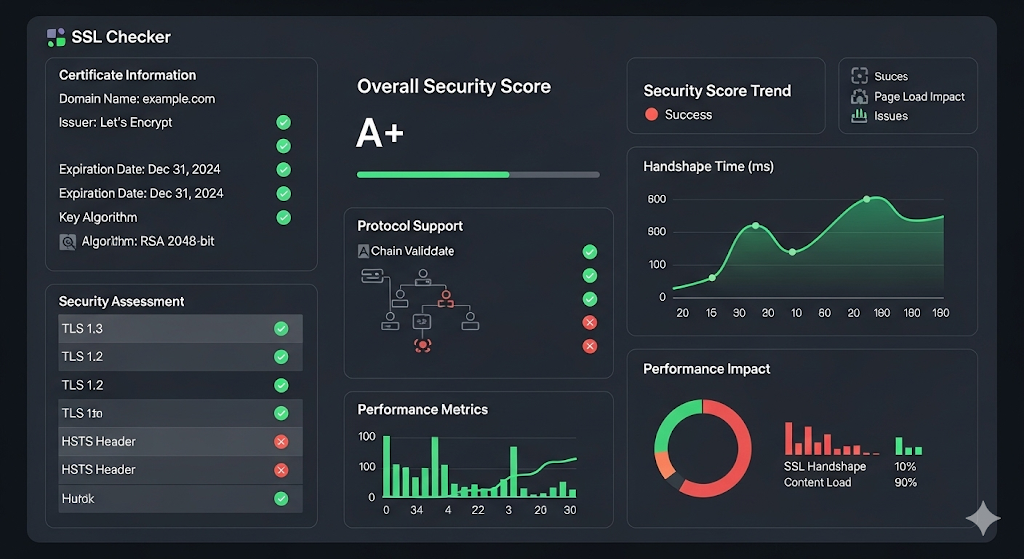
The SEOMagnate SSL Checker provides results in several sections, each offering valuable insights:
Certificate Information
This section displays basic details about your SSL certificate:
- Common Name: The primary domain name the certificate was issued for
- Issuer: The Certificate Authority that issued the certificate
- Validity Period: The start and expiration dates of the certificate
- Serial Number: The unique identifier for the certificate
- Signature Algorithm: The algorithm used to sign the certificate
- Key Strength: The bit length of the certificate's public key
Chain Validation
Here, you'll find information about the certificate chain:
- Root Certificate: Details about the root CA in your certificate chain
- Intermediate Certificates: Information about any intermediate certificates in the chain
- Chain Status: Whether the complete chain is properly configured and trusted
Protocol and Cipher Support
This section evaluates your SSL/TLS protocol and cipher suite configuration:
- Supported Protocols: Lists the SSL/TLS protocols your server supports (e.g., TLS 1.0, TLS 1.1, TLS 1.2, TLS 1.3)
- Cipher Suites: Details about the encryption algorithms your server supports
- Protocol Recommendations: Suggestions for which protocols to enable or disable for optimal security
- Cipher Recommendations: Guidance on cipher suite configuration to balance security and compatibility
Security Assessment
This critical section identifies potential security vulnerabilities:
- Known Vulnerabilities: Checks for common SSL/TLS vulnerabilities like Heartbleed, POODLE, BEAST, etc.
- Configuration Issues: Identifies problems with your SSL implementation that could weaken security
- Security Score: An overall rating of your SSL configuration's security posture
Performance Impact
This section evaluates how your SSL configuration affects website performance:
- Connection Time: Measures how long it takes to establish an SSL connection
- Handshake Time: Assesses the SSL handshake process efficiency
- Performance Recommendations: Suggestions for optimizing SSL performance without compromising security
Mobile Compatibility
This specialized section focuses on mobile-specific SSL considerations:
- Mobile Browser Support: Checks how your SSL implementation works across different mobile browsers
- Mobile Performance: Evaluates SSL performance on mobile devices and networks
- Mobile Recommendations: Suggestions for optimizing SSL for mobile users
Step-by-Step Guide to Fixing Common SSL Issues
Even with the best SSL checker tool, identifying issues is only half the battle. This section provides detailed, step-by-step instructions for resolving the most common SSL certificate problems.
Issue 1: Expired SSL Certificate
Symptoms:
- Browser security warnings about expired certificates
- SEOMagnate SSL Checker shows "Certificate Expired" status
- Website visitors see "Your connection is not private" warnings
Step-by-Step Solution:
Purchase or Renew Your Certificate:
- If you have an existing certificate, contact your provider to renew it
- If you need a new certificate, choose an appropriate type (DV, OV, or EV) based on your needs
- Consider free options like Let's Encrypt if appropriate for your website
Generate a Certificate Signing Request (CSR):
- Log in to your hosting control panel or server
- Navigate to the SSL/TLS management section
- Select "Generate CSR" or similar option
- Fill in the required information (domain name, organization details, etc.)
- Save the generated CSR code
Complete the Validation Process:
- Submit your CSR to your chosen Certificate Authority
- Complete the required validation (email, DNS, or file-based depending on certificate type)
- Wait for the CA to issue your certificate (time varies by certificate type)
Install the New Certificate:
- Once issued, download your certificate files (typically including the certificate, private key, and intermediate certificates)
- Log in to your hosting control panel or server
- Navigate to the SSL/TLS management section
- Select "Install SSL Certificate" or similar option
- Upload or paste the certificate files in the appropriate fields
- Save the installation
Verify the Installation:
- Use the SEOMagnate SSL Checker to verify your new certificate is properly installed
- Test your website in multiple browsers to ensure no security warnings appear
- Check all subdomains if using a wildcard certificate
Prevention Tips:
- Set calendar reminders for certificate expiration dates
- Enable auto-renewal if available with your certificate provider
- Consider using a certificate management tool for automated monitoring
Issue 2: Incomplete Certificate Chain
Symptoms:
- SEOMagnate SSL Checker shows "Incomplete Chain" warning
- Website works in some browsers but not others
- Some mobile devices show security warnings while desktop browsers don't
Step-by-Step Solution:
Identify Missing Certificates:
- Use the SEOMagnate SSL Checker to determine which intermediate certificates are missing
- Note the Certificate Authority that issued your certificate
Download Required Certificates:
- Visit your Certificate Authority's website
- Navigate to their repository of intermediate certificates
- Download the appropriate intermediate certificate bundle for your certificate type
- If unsure, contact your CA's support for assistance
Install the Intermediate Certificates:
- Log in to your hosting control panel or server
- Navigate to the SSL/TLS management section
- Look for an option to manage or install intermediate certificates
- Upload or paste the intermediate certificate content
- Save the changes
Restart Your Web Server:
- Some server configurations require a restart after certificate changes
- Access your server's command line or hosting control panel
- Restart the web server software (Apache, Nginx, IIS, etc.)
Verify the Fix:
- Use the SEOMagnate SSL Checker to confirm the chain is now complete
- Test your website on multiple browsers and devices
- Pay special attention to mobile browsers and older desktop browsers
Prevention Tips:
- When installing SSL certificates, always include the complete certificate bundle
- Use reputable hosting providers that handle certificate chain installation automatically
- Regularly check your certificate chain with an SSL checker tool
Issue 3: Mixed Content Errors
Symptoms:
- Browser shows "Mixed Content" warnings
- Padlock icon appears with a warning symbol or doesn't appear at all
- SEOMagnate SSL Checker identifies mixed content issues
- Some page elements fail to load
Step-by-Step Solution:
Identify Mixed Content:
- Use browser developer tools to identify mixed content:
- In Chrome: Right-click → Inspect → Security tab
- In Firefox: Right-click → Inspect → Security tab
- Look for resources loaded over HTTP instead of HTTPS
- Common culprits: images, scripts, stylesheets, iframes, and third-party widgets
Update Internal Links:
- For content hosted on your own domain:
- Update all internal links to use HTTPS instead of HTTP
- Replace absolute URLs (http://www.yourdomain.com/image.jpg) with protocol-relative URLs (//www.yourdomain.com/image.jpg) or relative URLs (/image.jpg)
- Update your website's configuration to enforce HTTPS
Update External Resources:
- For third-party resources:
- Check if the resource is available over HTTPS
- If available, update the URL to use HTTPS
- If not available over HTTPS, consider:
- Finding an alternative HTTPS-enabled resource
- Hosting the resource locally on your server
- Removing the resource if not essential
Update Database Content:
- If your website uses a database (WordPress, Drupal, etc.):
- Use a plugin or tool to update all HTTP URLs to HTTPS in your database
- Popular options: Better Search Replace (WordPress), Velvet Blues Update URLs (WordPress)
- Always backup your database before making bulk changes
Update Configuration Files:
- Update your website's configuration files to enforce HTTPS:
- For WordPress: Update site URL in Settings → General
- For other CMS: Update configuration files or settings
- For custom sites: Update .htaccess or server configuration files
Implement HTTP to HTTPS Redirects:
- Add redirect rules to force HTTPS connections:
- For Apache: Add to .htaccess file:
Line Wrapping
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]
- For Nginx: Add to server configuration:
Line Wrapping
server {
listen 80;
server_name yourdomain.com www.yourdomain.com;
return 301 https://$host$request_uri;
}
Verify the Fix:
- Use the SEOMagnate SSL Checker to confirm mixed content issues are resolved
- Test your website in multiple browsers
- Use online tools like Why No Padlock? (whynopadlock.com) for additional verification
Prevention Tips:
- Always use HTTPS URLs when adding new content
- Implement Content Security Policy (CSP) headers to prevent mixed content
- Regularly scan your website for mixed content issues
Issue 4: Protocol and Cipher Vulnerabilities
Symptoms:
- SEOMagnate SSL Checker identifies weak protocols or cipher suites
- Security scanners flag SSL/TLS vulnerabilities
- Website fails compliance requirements for security standards
Step-by-Step Solution:
Identify Vulnerable Protocols and Ciphers:
- Use the SEOMagnate SSL Checker to identify which protocols and cipher suites are causing issues
- Pay special attention to outdated protocols like SSLv2, SSLv3, and TLS 1.0
- Note any weak ciphers or those with known vulnerabilities
Access Server Configuration:
- Log in to your server via SSH or hosting control panel
- Locate your SSL/TLS configuration file:
- Apache: Typically in httpd.conf, ssl.conf, or a virtual host file
- Nginx: Typically in nginx.conf or a site configuration file
- IIS: Use IIS Manager to access SSL configuration
Update Protocol Configuration:
- Modify your SSL/TLS configuration to support only secure protocols:
- For Apache:
Line Wrapping
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
SSLProtocol +TLSv1.2 +TLSv1.3
- For Nginx:
Line Wrapping
ssl_protocols TLSv1.2 TLSv1.3;
- For IIS: Use IIS Manager to disable older protocols
Update Cipher Suite Configuration:
- Configure strong cipher suites:
- For Apache:
Line Wrapping
SSLCipherSuite HIGH:!aNULL:!MD5
SSLHonorCipherOrder on
- For Nginx:
Line Wrapping
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256';
ssl_prefer_server_ciphers on;
- For IIS: Use IIS Manager to configure cipher suites
Enable Additional Security Features:
- Add these security enhancements to your configuration:
- For Apache:
Line Wrapping
SSLCompression off
SSLUseStapling on
SSLStaplingCache "shmcb:logs/ssl_stapling(32768)"
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"
- For Nginx:
Line Wrapping
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
ssl_stapling on;
ssl_stapling_verify on;
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;
Restart Your Web Server:
- Apply the changes by restarting your web server:
- For Apache: sudo systemctl restart apache2 or sudo service httpd restart
- For Nginx: sudo systemctl restart nginx or sudo service nginx restart
- For IIS: Use IIS Manager to restart the site or application pool
Verify the Fix:
- Use the SEOMagnate SSL Checker to confirm vulnerabilities are resolved
- Test your website with multiple tools like Qualys SSL Labs' SSL Test
- Ensure your website still works across different browsers and devices
Prevention Tips:
- Stay informed about new SSL/TLS vulnerabilities and updates
- Regularly review and update your SSL/TLS configuration
- Consider using configuration management tools for consistent server settings
Issue 5: Certificate Name Mismatch
Symptoms:
- Browser warnings about certificate name mismatch
- SEOMagnate SSL Checker identifies hostname mismatch
- Certificate works for www.domain.com but not domain.com or vice versa
Step-by-Step Solution:
Identify the Mismatch:
- Use the SEOMagnate SSL Checker to determine which domain names are covered by your certificate
- Note the exact domain name you're trying to access
- Identify the difference between the certificate name and the accessed domain
Determine the Best Solution:
- Based on your needs, choose one of these approaches:
- Obtain a new certificate that covers all required domain names
- Set up redirects to direct traffic to the certificate-covered domain
- Use a multi-domain or wildcard certificate if you need to cover multiple domains or subdomains
Option A: Obtain a New Certificate:
- If you need a new certificate:
- Purchase or obtain a certificate that covers all required domains
- Generate a new CSR with the correct Common Name and Subject Alternative Names (SANs)
- Complete the validation process
- Install the new certificate following the steps in Issue 1
Option B: Set Up Redirects:
- If you want to redirect traffic to a single domain:
- Access your server configuration or .htaccess file
- Add redirect rules:
- For Apache (.htaccess):
Line Wrapping
RewriteEngine On
RewriteCond %{HTTP_HOST} ^domain\.com [NC]
RewriteRule ^(.*)$ https://www.domain.com/$1 [L,R=301]
- For Nginx:
Line Wrapping
server {
listen 80;
server_name domain.com;
return 301 https://www.domain.com$request_uri;
}
- Test the redirects to ensure they work correctly
Option C: Use a Multi-Domain or Wildcard Certificate:
- If you need to cover multiple domains or subdomains:
- Purchase a multi-domain (SAN) or wildcard certificate
- Generate a CSR with the appropriate names
- Complete validation for all domains
- Install the certificate following the steps in Issue 1
Verify the Fix:
- Use the SEOMagnate SSL Checker to confirm the certificate name matches the domain
- Test your website with and without www, and any subdomains
- Ensure all variations work correctly without warnings
Prevention Tips:
- When purchasing certificates, consider all domain variations you'll need
- Use wildcard certificates if you have many subdomains
- Implement consistent domain naming across your website
Advanced SSL Configuration for Enhanced Security
Beyond fixing common issues, optimizing your SSL configuration can significantly enhance your website's security and performance. This section covers advanced SSL configuration techniques that go beyond basic certificate installation.
HTTP Strict Transport Security (HSTS)
HSTS is a web security policy that helps protect websites against protocol downgrade attacks and cookie hijacking. It instructs browsers to only communicate with your site using HTTPS, automatically converting any HTTP requests to HTTPS.
Implementing HSTS
Basic HSTS Implementation:
- Add the HSTS header to your server configuration:
- For Apache:
Line Wrapping
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"
- For Nginx:
Line Wrapping
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;
- For IIS: Use the URL Rewrite module to add the header
Advanced HSTS Configuration:
- For enhanced security, add the preload directive:
Line Wrapping
Strict-Transport-Security: max-age=31536000; includeSubDomains; preload
- This tells browsers to only connect to your site using HTTPS, even before the first visit
HSTS Preloading:
- Submit your site to the HSTS preload list:
- Visit https://hstspreload.org/
- Check if your site meets the requirements
- Submit your domain for inclusion
- Once preloaded, your site will be hardcoded into browsers to only use HTTPS
HSTS Best Practices
- Start with a short max-age (e.g., 300 seconds) and gradually increase it
- Ensure your SSL configuration is working perfectly before implementing HSTS
- Test HSTS on a staging environment first
- Be aware that HSTS can make temporary SSL issues more difficult to resolve
Certificate Transparency
Certificate Transparency (CT) is an open framework for monitoring and auditing SSL certificates. It helps identify mistakenly or maliciously issued certificates and enhances the overall trust in the SSL ecosystem.
Implementing Certificate Transparency
Enable CT for Your Certificate:
- When obtaining or renewing your certificate, request CT inclusion
- Most major CAs now support CT by default
Add SCTs to Your Server Configuration:
- Signed Certificate Timestamps (SCTs) prove your certificate has been logged:
- For Apache:
Line Wrapping
SSLUseStapling on
SSLStaplingCache "shmcb:logs/ssl_stapling(32768)"
- For Nginx:
Line Wrapping
ssl_stapling on;
ssl_stapling_verify on;
Monitor Certificate Transparency Logs:
- Use tools like https://crt.sh/ to monitor certificates issued for your domain
- Set up alerts for new certificates to detect potential unauthorized issuances
Certificate Transparency Best Practices
- Always choose certificates that include SCTs
- Regularly monitor CT logs for your domain
- Consider implementing CT monitoring in your security operations
OCSP Stapling
Online Certificate Status Protocol (OCSP) Stapling improves SSL performance by allowing the server to provide proof of certificate validity directly, rather than requiring the browser to check with the Certificate Authority.
Implementing OCSP Stapling
Enable OCSP Stapling in Server Configuration:
- For Apache:
Line Wrapping
SSLUseStapling on
SSLStaplingCache "shmcb:logs/ssl_stapling(32768)"
- For Nginx:
Line Wrapping
ssl_stapling on;
ssl_stapling_verify on;
ssl_stapling_file /path/to/stapling_file;
Verify OCSP Stapling is Working:
- Use the SEOMagnate SSL Checker to verify OCSP stapling is enabled
- Test with command-line tools:
Line Wrapping
openssl s_client -connect yourdomain.com:443 -status
- Look for "OCSP Response Status" in the output
OCSP Stapling Best Practices
- Always enable OCSP stapling for improved performance
- Monitor your stapling cache to ensure it's working correctly
- Consider increasing the cache size for high-traffic websites
Perfect Forward Secrecy
Perfect Forward Secrecy (PFS) ensures that the compromise of a server's private key won't compromise past session keys. This is achieved by using ephemeral key exchange methods.
Implementing Perfect Forward Secrecy
Configure Cipher Suites for PFS:
- For Apache:
Line Wrapping
SSLCipherSuite HIGH:!aNULL:!MD5:!SEED:!IDEA:!RC4
SSLHonorCipherOrder on
- For Nginx:
Line Wrapping
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256';
ssl_prefer_server_ciphers on;
Verify PFS is Enabled:
- Use the SEOMagnate SSL Checker to verify PFS support
- Test with Qualys SSL Labs' SSL Test
Perfect Forward Secrecy Best Practices
- Prioritize ECDHE key exchange methods
- Regularly update your cipher suite configuration
- Test your configuration after each update
TLS 1.3 Implementation
TLS 1.3 is the latest version of the TLS protocol, offering improved security and performance over previous versions.
Implementing TLS 1.3
Check Server and Browser Support:
- Ensure your server software supports TLS 1.3:
- Apache 2.4.36+
- Nginx 1.13.0+
- OpenSSL 1.1.1+
- Verify that most of your visitors use browsers that support TLS 1.3
Enable TLS 1.3 in Server Configuration:
- For Apache:
Line Wrapping
SSLProtocol all -SSLv3 -TLSv1 -TLSv1.1 +TLSv1.2 +TLSv1.3
- For Nginx:
Line Wrapping
ssl_protocols TLSv1.2 TLSv1.3;
Configure TLS 1.3 Cipher Suites:
- TLS 1.3 has a simplified cipher suite structure:
- For Apache:
Line Wrapping
SSLCipherSuite TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256
- For Nginx:
Line Wrapping
ssl_ciphers 'TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256';
Verify TLS 1.3 is Working:
- Use the SEOMagnate SSL Checker to verify TLS 1.3 support
- Test with command-line tools:
Line Wrapping
openssl s_client -connect yourdomain.com:443 -tls1_3
TLS 1.3 Best Practices
- Enable TLS 1.3 alongside TLS 1.2 for maximum compatibility
- Take advantage of TLS 1.3 performance improvements
- Monitor your analytics to ensure visitor compatibility
SSL Performance Optimization
While SSL encryption is essential for security, it can impact website performance if not properly configured. This section covers techniques for optimizing SSL performance without compromising security.
SSL/TLS Handshake Optimization
The SSL/TLS handshake is the most performance-intensive part of establishing a secure connection. Optimizing this process can significantly reduce connection times.
Session Resumption
Session resumption allows clients to reuse previously established session parameters, eliminating the need for a full handshake.
Enable Session Tickets:
- For Apache:
Line Wrapping
SSLSessionTickets on
SSLSessionTicketKeyFile /path/to/ticketkey
- For Nginx:
Line Wrapping
ssl_session_tickets on;
ssl_session_ticket_key /path/to/ticketkey;
Configure Session Cache:
- For Apache:
Line Wrapping
SSLSessionCache shmcb:/path/to/cache(512000)
SSLSessionCacheTimeout 300
- For Nginx:
Line Wrapping
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
False Start
False Start allows the client to start sending encrypted data before the handshake is complete, reducing perceived latency.
Enable False Start:
- For Apache:
Line Wrapping
SSLFalseStart on
- For Nginx:
Line Wrapping
ssl_early_data on;
Verify False Start is Working:
- Use browser developer tools to check connection timing
- Look for reduced TLS connection times
HTTP/2 Implementation
HTTP/2 is a major revision of the HTTP protocol that offers significant performance improvements, especially when combined with SSL/TLS.
Implementing HTTP/2
Check Server Support:
- Ensure your server software supports HTTP/2:
- Apache 2.4.17+ with mod_http2
- Nginx 1.9.5+ with http_v2_module
Enable HTTP/2 in Server Configuration:
- For Apache:
Line Wrapping
Protocols h2 http/1.1
- For Nginx:
Line Wrapping
listen 443 ssl http2;
Verify HTTP/2 is Working:
- Use browser developer tools to check the protocol
- Use online tools like https://tools.keycdn.com/http2-test
HTTP/2 Best Practices
- Combine HTTP/2 with SSL/TLS for optimal performance
- Take advantage of HTTP/2 features like multiplexing and server push
- Monitor your website's performance after implementing HTTP/2
Resource Optimization for HTTPS
Optimizing how resources are loaded can further improve SSL performance.
Resource Hinting
Resource hints give browsers information about resources they'll need soon, allowing them to optimize loading.
Implement Preconnect:
- Add preconnect hints for third-party resources:
Implement DNS-Prefetch:
- Add DNS prefetching for third-party domains:
Implement Preload:
- Add preload directives for critical resources:
Caching Optimization
Proper caching reduces the need for repeated SSL handshakes.
Implement HTTP Caching Headers:
- Add cache-control headers for static resources:
Line Wrapping
ExpiresActive on
ExpiresByType text/css "access plus 1 year"
ExpiresByType application/javascript "access plus 1 year"
ExpiresByType image/jpeg "access plus 1 year"
ExpiresByType image/png "access plus 1 year"
ExpiresByType image/svg+xml "access plus 1 year"
ExpiresByType image/webp "access plus 1 year"
ExpiresByType font/woff2 "access plus 1 year"
Implement Service Workers:
- Create a service worker for offline functionality and caching:
javascript
Line Wrapping
const CACHE_NAME = 'my-site-cache-v1';
const urlsToCache = [
'/',
'/styles/main.css',
'/scripts/main.js'
];
self.addEventListener('install', event => {
event.waitUntil(
caches.open(CACHE_NAME)
.then(cache => cache.addAll(urlsToCache))
);
});
self.addEventListener('fetch', event => {
event.respondWith(
caches.match(event.request)
.then(response => {
return response || fetch(event.request);
})
);
});
Content Delivery Network (CDN) Integration
Using a CDN with SSL can significantly improve performance by serving content from locations closer to your visitors.
Choose a CDN with SSL Support:
- Select a CDN provider that offers:
- Free SSL certificates
- HTTP/2 support
- Global edge locations
- Easy integration with your origin server
Configure CDN SSL:
- Choose between flexible, full, or strict SSL modes
- Ensure your CDN properly handles certificate renewal
- Configure origin-pull protection if needed
Verify CDN SSL Implementation:
- Use the SEOMagnate SSL Checker to verify your CDN's SSL configuration
- Test performance from different geographic locations
Mobile-Specific SSL Considerations
With the majority of internet traffic now coming from mobile devices, optimizing SSL for mobile is crucial. This section covers mobile-specific SSL considerations and best practices.
Mobile Browser SSL Support
Mobile browsers have different SSL/TLS support characteristics compared to desktop browsers.
Understanding Mobile Browser Fragmentation
iOS Safari:
- Generally has excellent SSL/TLS support
- Quickly adopts new protocols like TLS 1.3
- Strict about certificate validation
Android Chrome:
- Follows desktop Chrome's SSL/TLS support
- Good support for modern protocols and cipher suites
- Regular security updates
Android Default Browser:
- Varies by Android version and manufacturer
- Older versions may have limited SSL/TLS support
- May not support the latest security features
Mobile Firefox and Opera:
- Generally good SSL/TLS support
- Regular security updates
- May have different default configurations
Optimizing for Mobile Browser Compatibility
Support Legacy Protocols Cautiously:
- While TLS 1.2 and 1.3 are recommended, consider supporting TLS 1.1 for older mobile devices:
Line Wrapping
ssl_protocols TLSv1.1 TLSv1.2 TLSv1.3;
Use Mobile-Friendly Cipher Suites:
- Prioritize cipher suites that work well on mobile devices:
Line Wrapping
ssl_ciphers 'ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305';
Test on Real Mobile Devices:
- Use services like BrowserStack or Sauce Labs to test on real mobile devices
- Pay special attention to older Android devices
- Test on both cellular and Wi-Fi connections
Mobile Network Performance
Mobile networks have different characteristics than fixed-line connections, affecting SSL performance.
Understanding Mobile Network Challenges
Higher Latency:
- Mobile networks typically have higher latency than fixed-line connections
- This makes SSL handshakes more noticeable to users
- Packet loss can further degrade performance
Variable Bandwidth:
- Mobile bandwidth can vary significantly based on signal strength
- Switching between Wi-Fi and cellular networks can cause interruptions
- Network congestion can impact SSL performance
Battery Life Considerations:
- SSL operations consume device battery
- Complex cipher suites can increase battery usage
- Frequent reconnections due to network changes can drain battery
Optimizing SSL for Mobile Networks
Minimize Handshakes:
- Implement session resumption to reduce handshakes:
Line Wrapping
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 1d;
ssl_session_tickets on;
Optimize Certificate Chain:
- Use a short certificate chain to reduce handshake size
- Consider ECDSA certificates which are smaller than RSA
- Remove unnecessary intermediate certificates
Implement HTTP/2:
- HTTP/2's multiplexing reduces the impact of high latency
- Server push can proactively send critical resources
- Header compression reduces overhead
Use Adaptive Bitrate:
- For media content, implement adaptive bitrate streaming
- Adjust quality based on network conditions
- Prioritize critical resources on slow connections
Mobile App SSL Implementation
If you have a mobile app that communicates with your server, special SSL considerations apply.
Mobile App SSL Best Practices
Implement Certificate Pinning:
- For iOS:
swift
Line Wrapping
let serverTrustPolicy = ServerTrustPolicy.pinCertificates(
certificates: ServerTrustPolicy.certificates(),
validateCertificateChain: true,
validateHost: true
)
- For Android:
java
Line Wrapping
CertificatePinner certificatePinner = new CertificatePinner.Builder()
.add("yourdomain.com", "sha256/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=")
.build();
Handle SSL Errors Gracefully:
- Provide clear error messages for SSL issues
- Offer guidance for resolving common problems
- Allow users to contact support if needed
Support Network Changes:
- Handle network switches gracefully
- Re-establish secure connections when network conditions change
- Implement appropriate retry logic for failed connections
Optimize Data Transfer:
- Minimize data transfer to reduce battery usage
- Use efficient data formats like Protocol Buffers
- Implement compression where appropriate
SSL for Different Platforms and Environments
SSL implementation can vary significantly depending on your hosting environment, platform, or content management system. This section provides platform-specific SSL guidance.
WordPress SSL Implementation
WordPress powers over 40% of websites, making it one of the most common platforms for SSL implementation.
WordPress SSL Setup
Install SSL Certificate:
- Obtain and install an SSL certificate through your hosting provider
- Many WordPress hosts offer free SSL certificates via Let's Encrypt
Update WordPress Settings:
- Go to Settings → General
- Update both WordPress Address and Site Address to use HTTPS
- Save changes
Update Content Links:
- Use a plugin like Better Search Replace to update HTTP links to HTTPS in your database
- Search for: http://yourdomain.com
- Replace with: https://yourdomain.com
- Always backup your database before making changes
Implement Mixed Content Fixing:
- Install a plugin like SSL Insecure Content Fixer to handle mixed content
- Configure the plugin to fix mixed content automatically
- Test your site to ensure all resources load securely
Set Up Redirects:
- Add redirect rules to your .htaccess file:
Line Wrapping
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]
WordPress SSL Best Practices
- Use security plugins that support SSL
- Regularly check for mixed content issues
- Implement HTTP Strict Transport Security (HSTS)
- Use a caching plugin that works well with HTTPS
- Consider using a CDN with SSL support
E-commerce Platform SSL Implementation
E-commerce platforms have special SSL requirements due to the handling of sensitive payment information.
Shopify SSL Implementation
Shopify's Built-in SSL:
- All Shopify stores automatically include SSL certificates
- No additional configuration is required
- Shopify handles certificate renewal and maintenance
Custom Domain SSL:
- If using a custom domain, ensure DNS is configured correctly
- Verify SSL status in Shopify admin under Online Store → Domains
- Wait for SSL provisioning (usually 24-48 hours)
WooCommerce SSL Implementation
Install SSL Certificate:
- Obtain and install an SSL certificate for your WordPress site
- Follow the WordPress SSL setup steps above
Configure WooCommerce for SSL:
- Go to WooCommerce → Settings
- Check "Force HTTPS when checking out"
- Check "Force HTTPS on the checkout page"
- Save changes
Update Payment Gateway Settings:
- Ensure all payment gateways are configured to use HTTPS endpoints
- Update any webhook URLs to use HTTPS
- Test payment processing in sandbox mode
Magento SSL Implementation
Install SSL Certificate:
- Obtain and install an SSL certificate for your Magento site
- Ensure your hosting environment is properly configured for SSL
Configure Magento for SSL:
- Go to Stores → Configuration → General → Web
- Set Base URL and Secure Base URL to use HTTPS
- Set "Use Secure URLs on Storefront" to Yes
- Set "Use Secure URLs in Admin" to Yes
- Save changes
Clear Cache:
- Clear Magento cache after making changes
- Use the command: bin/magento cache:clean
- Verify that all pages load correctly with HTTPS
E-commerce SSL Best Practices
- Always use Extended Validation (EV) certificates for maximum trust
- Implement HSTS to ensure all connections use HTTPS
- Regularly scan for mixed content issues
- Use a Web Application Firewall (WAF) for additional security
- Ensure all third-party payment integrations use HTTPS
Cloud Platform SSL Implementation
Cloud platforms like AWS, Google Cloud, and Azure have specific SSL implementation processes.
AWS SSL Implementation
AWS Certificate Manager (ACM):
- Go to AWS Certificate Manager in the AWS Console
- Request a public certificate
- Add your domain names
- Choose DNS validation
- Create CNAME records in your DNS to validate domain ownership
Load Balancer SSL Configuration:
- Go to EC2 → Load Balancers
- Select your load balancer
- Go to Listeners tab
- Add an HTTPS listener on port 443
- Select your ACM certificate
- Configure security policy as needed
CloudFront SSL Configuration:
- Go to CloudFront → Distributions
- Select your distribution
- Go to Viewer tab
- Set Viewer Protocol Policy to Redirect HTTP to HTTPS
- Select your ACM certificate
Google Cloud SSL Implementation
Google Cloud Load Balancing SSL:
- Go to Network Services → Load Balancing
- Select your load balancer
- Go to Frontend configuration
- Set Protocol to HTTPS
- Create or select an SSL certificate
- Configure SSL policy as needed
Cloud Storage SSL:
- For static websites hosted on Cloud Storage:
- Enable uniform bucket-level access
- Set up a load balancer with SSL termination
- Configure the load balancer to point to your Cloud Storage bucket
Azure SSL Implementation
Azure App Service SSL:
- Go to App Service → TLS/SSL settings
- Add a binding for HTTPS
- Select or upload an SSL certificate
- Set HTTPS Only to On
Azure Application Gateway SSL:
- Go to Application Gateway → Listeners
- Add an HTTPS listener
- Select or upload an SSL certificate
- Configure SSL policy as needed
Cloud Platform SSL Best Practices
- Use managed certificate services where available
- Implement proper SSL termination at load balancers
- Use SSL policies that balance security and compatibility
- Set up automatic certificate renewal
- Monitor SSL certificate expiration dates
Monitoring and Maintaining SSL Certificates
Implementing SSL is not a one-time task. Ongoing monitoring and maintenance are essential to ensure continuous security and avoid service disruptions. This section covers best practices for SSL certificate monitoring and maintenance.
SSL Certificate Monitoring Strategies
Proactive monitoring can prevent certificate-related issues before they impact your users.
Automated Monitoring Tools
SEOMagnate SSL Checker:
- Regularly use the SEOMagnate SSL Checker to monitor your certificates
- Set up scheduled checks for critical domains
- Review detailed reports for potential issues
Nagios or Zabbix:
- Configure monitoring plugins to check SSL certificate expiration
- Set up alerts for certificates approaching expiration
- Monitor SSL/TLS protocol support and configuration
UptimeMonster or StatusCake:
- Use these services to monitor SSL certificate status
- Set up email and SMS alerts for certificate issues
- Integrate with team communication tools like Slack
Custom Monitoring Solutions
OpenSSL Script:
- Create a script to check certificate expiration:
bash
Line Wrapping
#!/bin/bash
DOMAIN="yourdomain.com"
EXPIRY_DATE=$(echo | openssl s_client -connect $DOMAIN:443 2>/dev/null | openssl x509 -noout -dates | grep notAfter | cut -d= -f2)
EXPIRY_TIMESTAMP=$(date -d "$EXPIRY_DATE" +%s)
CURRENT_TIMESTAMP=$(date +%s)
DAYS_LEFT=$(( ($EXPIRY_TIMESTAMP - $CURRENT_TIMESTAMP) / 86400 ))
if [ $DAYS_LEFT -lt 30 ]; then
echo "SSL certificate for $DOMAIN expires in $DAYS_LEFT days!"
# Add alert logic here
fi
Python Monitoring Script:
- Use Python's ssl module for more advanced monitoring:
python
Line Wrapping
import ssl
import socket
import datetime
def check_ssl_cert(hostname, port=443):
context = ssl.create_default_context()
with socket.create_connection((hostname, port)) as sock:
with context.wrap_socket(sock, server_hostname=hostname) as ssock:
cert = ssock.getpeercert()
expiry_date = datetime.datetime.strptime(cert['notAfter'], '%b %d %H:%M:%S %Y %Z')
days_left = (expiry_date - datetime.datetime.now()).days
return {
'hostname': hostname,
'expires': expiry_date,
'days_left': days_left,
'issuer': dict(x[0] for x in cert['issuer'])['organizationName'],
'subject': dict(x[0] for x in cert['subject'])['commonName']
}
result = check_ssl_cert('yourdomain.com')
print(f"Certificate for {result['hostname']} expires in {result['days_left']} days")
Monitoring Best Practices
- Monitor all certificates, including those for subdomains and internal services
- Set up alerts at multiple thresholds (e.g., 60 days, 30 days, 7 days before expiration)
- Monitor not just expiration but also configuration and security issues
- Document your monitoring procedures and escalation paths
SSL Certificate Maintenance
Regular maintenance ensures your SSL implementation remains secure and up-to-date.
Certificate Renewal Process
Standard Renewal Process:
- Begin renewal process 30-60 days before expiration
- Generate a new CSR with the same information as the current certificate
- Submit the CSR to your Certificate Authority
- Complete the validation process
- Install the new certificate following your platform-specific procedures
- Verify the installation using the SEOMagnate SSL Checker
Automated Renewal with Let's Encrypt:
- Install Certbot for automated Let's Encrypt certificate management:
bash
Line Wrapping
sudo apt-get update
sudo apt-get install certbot
- Set up automatic renewal:
bash
Line Wrapping
sudo certbot renew --dry-run
sudo systemctl status certbot.timer
- Test the renewal process to ensure it works correctly
Configuration Updates
Regular Security Reviews:
- Quarterly reviews of your SSL/TLS configuration
- Check for new vulnerabilities and best practices
- Update protocols and cipher suites as needed
- Test changes in a staging environment first
Performance Optimization:
- Regularly review SSL performance metrics
- Optimize handshake times and session resumption
- Implement new performance-enhancing features like TLS 1.3
- Monitor the impact of configuration changes
Documentation and Knowledge Management
Maintain SSL Inventory:
- Keep an inventory of all SSL certificates, including:
- Domain names
- Certificate authorities
- Expiration dates
- Installation locations
- Responsible parties
Document Procedures:
- Create step-by-step procedures for common SSL tasks
- Include troubleshooting guides for common issues
- Store documentation in an accessible location
- Regularly review and update documentation
Disaster Recovery for SSL Issues
Even with the best monitoring and maintenance, SSL issues can still occur. Having a disaster recovery plan can minimize downtime and user impact.
Common SSL Disasters and Recovery
Expired Certificate:
- Symptoms: Browser warnings, service disruption
- Immediate Action: Renew certificate immediately using expedited process if available
- Prevention: Implement automated monitoring and renewal
Compromised Private Key:
- Symptoms: Security breach, potential data exposure
- Immediate Action: Revoke certificate immediately, generate new key pair, issue new certificate
- Prevention: Secure private key storage, limit access to private keys
Configuration Error:
- Symptoms: Service disruption, browser warnings
- Immediate Action: Revert to last known good configuration, investigate and fix error
- Prevention: Test configuration changes in staging, implement configuration management
Disaster Recovery Planning
Create a Response Team:
- Identify team members responsible for SSL issues
- Define roles and responsibilities
- Establish communication channels
- Conduct regular training and drills
Develop Response Procedures:
- Create step-by-step procedures for common SSL disasters
- Include decision trees for complex scenarios
- Document escalation paths
- Include contact information for certificate providers
Test Your Plan:
- Conduct regular disaster recovery drills
- Test response to simulated SSL issues
- Evaluate team performance
- Update procedures based on lessons learned
The Future of SSL/TLS and Website Security
The SSL/TLS landscape continues to evolve, with new protocols, standards, and best practices emerging regularly. This section explores the future of SSL/TLS and website security to help you prepare for what's ahead.
Emerging SSL/TLS Technologies
Several new technologies are shaping the future of SSL/TLS and website security.
TLS 1.3 Adoption
TLS 1.3 represents a significant improvement over previous versions, with enhanced security and performance.
Key TLS 1.3 Improvements:
- Simplified handshake process reduces latency
- Removed insecure features like compression and renegotiation
- Improved forward secrecy
- Zero Round Trip Time (0-RTT) mode for faster subsequent connections
Adoption Status:
- Major browsers now support TLS 1.3
- Server software support is widespread
- Certificate authorities are fully compatible
- Some legacy systems may still require older protocol versions
Implementation Considerations:
- Test compatibility with all user agents
- Consider supporting TLS 1.2 alongside 1.3 for broader compatibility
- Monitor performance improvements after implementation
- Update cipher suite configurations for TLS 1.3
Post-Quantum Cryptography
Quantum computing poses a potential threat to current cryptographic standards, including SSL/TLS.
The Quantum Threat:
- Quantum computers could break current public-key cryptography
- RSA and ECC algorithms would be vulnerable
- Timeline estimates vary, but preparation is needed now
Post-Quantum Cryptography Standards:
- NIST is standardizing post-quantum cryptographic algorithms
- Lattice-based cryptography shows promise
- Hash-based signatures offer quantum resistance
- Standardization expected to complete in the next few years
Preparation Strategies:
- Implement crypto-agility in your systems
- Stay informed about post-quantum standards
- Plan for hybrid certificate approaches
- Consider longer-term certificate validity to ease transition
Certificate Authority Innovation
Certificate Authorities are developing new approaches to improve security and trust.
Short-Lived Certificates:
- Certificates with validity periods of days instead of years
- Automated issuance and renewal processes
- Reduced impact of compromised certificates
- Requires robust automation infrastructure
Automated Certificate Management Environment (ACME):
- Protocol for automated certificate issuance and renewal
- Popularized by Let's Encrypt
- Being adopted by other certificate authorities
- Enables fully automated certificate lifecycle management
New Validation Methods:
- DNS-based validation becoming more common
- Multi-factor authentication for high-assurance certificates
- Continuous validation rather than one-time checks
- Improved methods to prevent certificate misissuance
Regulatory and Compliance Trends
Regulatory changes continue to shape SSL/TLS requirements and best practices.
Data Protection Regulations
GDPR and SSL/TLS:
- GDPR emphasizes encryption as a security measure
- SSL/TLS is considered essential for protecting personal data
- Data breach notification requirements make SSL more critical
- Fines for non-compliance can be substantial
CCPA and Other Privacy Laws:
- Similar to GDPR, emphasizes data protection
- SSL/TLS implementation is part of compliance
- Consumer rights related to data security
- Evolving enforcement and interpretation
Industry-Specific Regulations:
- PCI DSS continues to evolve with stricter SSL/TLS requirements
- HIPAA in healthcare emphasizes encryption of protected health information
- Financial regulations increasingly mandate strong encryption
- Sector-specific requirements will continue to drive SSL/TLS adoption
Security Standards and Frameworks
Security Standards Evolution:
- NIST guidelines regularly updated to reflect new threats
- ISO 27001 emphasizes encryption as a security control
- CIS benchmarks include SSL/TLS configuration guidance
- Industry-specific security frameworks incorporate SSL/TLS requirements
Compliance Automation:
- Tools for automated compliance checking
- Continuous compliance monitoring
- Integration with security information and event management (SIEM) systems
- Automated remediation of compliance issues
Future Best Practices
Based on emerging trends and technologies, here are best practices to prepare for the future of SSL/TLS.
Strategic Planning
Develop a Cryptographic Agility Strategy:
- Design systems that can adapt to new cryptographic standards
- Avoid hard-coded cryptographic algorithms
- Implement modular cryptographic components
- Regularly review and update cryptographic policies
Invest in Automation:
- Automate certificate issuance, renewal, and revocation
- Implement automated configuration management
- Use infrastructure as code for SSL/TLS configurations
- Build automated testing and validation processes
Plan for Protocol Evolution:
- Stay informed about new protocol developments
- Test new protocols in non-production environments
- Plan migration strategies for protocol transitions
- Monitor industry adoption of new standards
Technical Implementation
Implement Modern Security Headers:
- HTTP Strict Transport Security (HSTS)
- Content Security Policy (CSP)
- Expect-CT and Report-URI for certificate transparency
- Feature Policy to control browser features
Adopt Zero Trust Security Models:
- Verify every connection regardless of network location
- Implement mutual TLS where appropriate
- Use certificate-based authentication
- Continuously validate security posture
Enhance Monitoring and Visibility:
- Implement comprehensive SSL/TLS monitoring
- Collect and analyze SSL/TLS telemetry
- Use machine learning for anomaly detection
- Integrate with broader security monitoring systems
Organizational Preparedness
Build Security Expertise:
- Train staff on SSL/TLS best practices
- Stay current with emerging threats and technologies
- Participate in security communities and forums
- Consider specialized training for key personnel
Update Policies and Procedures:
- Regularly review SSL/TLS policies
- Update incident response procedures
- Document configuration standards
- Establish clear roles and responsibilities
Foster a Security Culture:
- Emphasize the importance of encryption and security
- Encourage reporting of potential issues
- Recognize and reward security improvements
- Make security a shared responsibility
Frequently Asked Questions About SSL Checker Online Tools
1. What is an SSL certificate and why do I need one?
An SSL (Secure Sockets Layer) certificate is a digital certificate that authenticates a website's identity and enables an encrypted connection. You need an SSL certificate to:
- Protect sensitive data transmitted between your website and visitors
- Build trust with your visitors through visual security indicators
- Improve your search engine rankings (Google uses HTTPS as a ranking signal)
- Avoid browser warnings that can drive away visitors
- Comply with data protection regulations like GDPR and CCPA
2. How does an SSL checker online tool work?
An SSL checker online tool works by:
- Establishing a connection to your web server on port 443 (the standard HTTPS port)
- Requesting and examining your SSL certificate
- Validating the certificate chain from your certificate to the root certificate authority
- Checking the certificate's expiration date, issuing authority, and domain name
- Analyzing your SSL/TLS configuration, including supported protocols and cipher suites
- Testing for known vulnerabilities and configuration issues
- Generating a comprehensive report with findings and recommendations
3. What information does an SSL checker provide?
A comprehensive SSL checker like SEOMagnate's tool provides:
- Certificate details (issuer, validity period, domain name, etc.)
- Certificate chain validation status
- Supported SSL/TLS protocols
- Configured cipher suites
- Security vulnerability assessment
- Performance impact analysis
- Mobile compatibility information
- Expiration date tracking
- Actionable recommendations for improvement
4. How often should I check my SSL certificate?
You should check your SSL certificate:
- At least once a month for routine monitoring
- Immediately after making any SSL-related configuration changes
- Before your certificate's expiration date (begin checking 60 days in advance)
- If you receive any security warnings or browser errors
- After any server or hosting changes
- As part of your regular security audits
5. Can I fix SSL issues myself, or do I need a developer?
Many SSL issues can be fixed without a developer, including:
- Installing or renewing SSL certificates through hosting control panels
- Fixing mixed content issues using plugins or tools
- Setting up basic redirects from HTTP to HTTPS
- Using SSL checker tools to identify and understand issues
However, you may need a developer for:
- Complex server configuration changes
- Custom application integration issues
- Advanced security implementations
- Troubleshooting persistent or unusual problems
- Implementing performance optimizations
6. What's the difference between SSL and TLS?
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are both cryptographic protocols designed to provide secure communications over a network. The key differences are:
- SSL is the older protocol, while TLS is its successor
- SSL has known vulnerabilities and is considered deprecated
- TLS offers stronger security algorithms and improved protocols
- TLS 1.0 was based on SSL 3.0, but subsequent versions have introduced significant improvements
- Modern systems should use TLS 1.2 or TLS 1.3, not SSL
Despite these technical differences, "SSL certificate" remains the commonly used term for certificates that actually implement TLS protocols.
7. How long does it take for SSL to activate?
SSL activation time varies depending on the certificate type:
- Domain Validated (DV) certificates: Typically activate within minutes to a few hours
- Organization Validated (OV) certificates: Usually take 1-3 days for validation
- Extended Validation (EV) certificates: Can take 1-2 weeks due to extensive validation
After installation, SSL should be active immediately, though DNS propagation may take up to 24 hours in some cases. You can verify activation using an SSL checker tool.
8. Can I get SSL for free?
Yes, you can get SSL certificates for free through:
- Let's Encrypt: A nonprofit Certificate Authority offering free DV certificates
- Cloudflare: Provides free SSL certificates for websites using their CDN
- Some hosting providers include free SSL certificates with their plans
- Certain website builders like WordPress.com and Wix offer free SSL
Free certificates typically provide basic encryption and domain validation but may lack some features of paid certificates, such as warranty protection or extended validation.
9. What happens when my SSL certificate expires?
When your SSL certificate expires:
- Browsers will display prominent security warnings to visitors
- Some browsers may prevent users from accessing your site entirely
- Search engines may flag your site as insecure
- Trust in your website will be significantly diminished
- You may experience a drop in traffic and conversions
To avoid these issues, renew your certificate before it expires and use monitoring tools to track expiration dates.
10. How do I know if my SSL certificate is working?
You can verify if your SSL certificate is working by:
- Looking for the padlock icon in your browser's address bar
- Checking that your URL begins with "https://" instead of "http://"
- Using an SSL checker tool like SEOMagnate's for comprehensive validation
- Testing your website on multiple browsers and devices
- Checking browser developer tools for any security warnings
11. Does SSL affect website speed?
SSL can affect website speed, but modern implementations minimize performance impact:
- The initial SSL handshake adds some latency to the first connection
- Modern protocols like TLS 1.3 reduce handshake overhead
- HTTP/2 (which requires HTTPS) can actually improve performance
- Technologies like OCSP stapling and session resumption optimize SSL performance
- The security benefits far outweigh the minimal performance impact
Proper SSL configuration can actually improve performance through HTTP/2 support and better caching.
12. What are common SSL certificate errors?
Common SSL certificate errors include:
- Expired certificates
- Certificate name mismatch (certificate issued for different domain)
- Incomplete certificate chain (missing intermediate certificates)
- Self-signed certificates not trusted by browsers
- Mixed content (loading HTTP resources on HTTPS pages)
- Protocol or cipher suite misconfigurations
- Certificate revocation or trust issues
- Incorrect installation or server configuration
13. How do I migrate from HTTP to HTTPS?
To migrate from HTTP to HTTPS:
- Install an SSL certificate on your server
- Update all internal links to use HTTPS
- Set up 301 redirects from HTTP to HTTPS
- Update your website's configuration to use HTTPS URLs
- Update external links and resources where possible
- Update your sitemap and submit it to search engines
- Implement HTTP Strict Transport Security (HSTS)
- Monitor for mixed content issues and fix them
- Update any third-party integrations or APIs
- Verify the migration using an SSL checker tool
14. What is mixed content and how does it affect SSL?
Mixed content occurs when a website loaded over HTTPS includes resources (images, scripts, stylesheets, etc.) loaded over HTTP. This affects SSL by:
- Breaking the padlock indicator in browsers
- Potentially causing security warnings
- Creating vulnerabilities that could compromise security
- Reducing user trust in your website
- Negatively impacting your SEO efforts
To fix mixed content, ensure all resources are loaded over HTTPS or use protocol-relative URLs.
15. How do I choose the right SSL certificate for my website?
To choose the right SSL certificate, consider:
- Validation Level: DV for basic encryption, OV for business verification, EV for maximum trust
- Coverage: Single domain, wildcard (for subdomains), or multi-domain (for multiple domains)
- Budget: Free options like Let's Encrypt for basic needs, paid certificates for additional features
- Website Type: E-commerce sites typically need higher validation than personal blogs
- Technical Requirements: Some applications have specific certificate requirements
- Browser Support: Ensure your certificate is compatible with all target browsers
For most small to medium websites, a free or low-cost DV certificate is sufficient. E-commerce and business sites should consider OV or EV certificates for enhanced trust.
Conclusion: Ensuring Website Security with SSL Checker Online Tools
In today's digital landscape, SSL encryption is no longer optional—it's a fundamental requirement for any website that values security, trust, and visibility. Throughout this comprehensive guide, we've explored the critical importance of SSL certificates, the various types available, and how to properly implement and maintain them. We've also examined common SSL issues and their solutions, advanced configuration techniques, and platform-specific considerations.
The key takeaways from this guide are clear:
SSL Implementation is Essential: Every website needs SSL encryption to protect data, build trust, and maintain search visibility.
Regular Monitoring is Critical: SSL certificates require ongoing monitoring to ensure they remain valid, properly configured, and secure.
Proper Configuration Matters: Simply having an SSL certificate isn't enough—proper configuration is essential for both security and performance.
Tools Make the Difference: A comprehensive ssl checker online tool like SEOMagnate's can identify issues, provide detailed analysis, and offer actionable recommendations.
The Landscape Continues to Evolve: SSL/TLS technologies continue to advance, and staying current with best practices is essential for long-term security.
By implementing the strategies and techniques outlined in this guide, you can ensure your website maintains robust security, builds trust with visitors, and performs well in search rankings. Remember that SSL security is not a one-time implementation but an ongoing process that requires attention, monitoring, and maintenance.
Take the first step toward comprehensive website security by using the SEOMagnate SSL Checker to analyze your current SSL implementation. Identify potential issues, understand your configuration, and implement the recommendations to enhance your website's security posture. Your visitors—and your search rankings—will thank you.
Author
John Smith is a cybersecurity specialist with over 15 years of experience in website security and SSL/TLS implementation. As a certified information systems security professional (CISSP), John has helped hundreds of businesses secure their online presence and protect sensitive customer data. He regularly contributes to security publications and speaks at industry conferences about the importance of encryption and secure communications. John's practical approach to complex security topics makes him a trusted resource for businesses of all sizes looking to enhance their website security posture.
